April/2020 New Braindump2go 300-715 Exam Dumps with PDF and VCE Free Updated Today! Following are some new 300-715 Exam Questions!
New Question
If a user reports a device lost or stolen, which portal should be used to prevent the device from accessing the network while still providing information about why the device is blocked?
A. Client Provisioning
B. Guest
C. BYOD
D. Blacklist
Answer: D
Explanation:
https://www.cisco.com/c/en/us/td/docs/solutions/Enterprise/Borderless_Networks/Unified_Access/BY OD_Design_Guide/Managing_Lost_or_Stolen_Device.html#90273
The Blacklist identity group is system generated and maintained by ISE to prevent access to lost or stolen devices. In this design guide, two authorization profiles are used to enforce the permissions for wireless and wired devices within the Blacklist:
Blackhole WiFi Access
Blackhole Wired Access
New Question
A user reports that the RADIUS accounting packets are not being seen on the Cisco ISE server. Which command is the user missing in the switch’s configuration?
A. radius-server vsa send accounting
B. aaa accounting network default start-stop group radius
C. aaa accounting resource default start-stop group radius
D. aaa accounting exec default start-stop group radios
Answer: A
New Question
Which two task types are included in the Cisco ISE common tasks support for TACACS+ profiles? (Choose two.)
A. Firepower
B. WLC
C. IOS
D. ASA
E. Shell
Answer: BE
Explanation:
https://www.cisco.com/c/en/us/td/docs/security/ise/2-
1/admin_guide/b_ise_admin_guide_21/b_ise_admin_guide_20_chapter_0100010.html
TACACS+ Profile
TACACS+ profiles control the initial login session of the device administrator. A session refers to each individual authentication, authorization, or accounting request. A session authorization request to a network device elicits an ISE response. The response includes a token that is interpreted by the network device, which limits the commands that may be executed for the duration of a session. The authorization policy for a device administration access service can contain a single shell profile and multiple command sets. The TACACS+ profile definitions are split into two components:
Common tasks
Custom attributes
There are two views in the TACACS+ Profiles page (Work Centers > Device Administration > Policy Elements > Results > TACACS Profiles)–Task Attribute View and Raw View. Common tasks can be entered using the Task Attribute View and custom attributes can be created in the Task Attribute View as well as the Raw View.
The Common Tasks section allows you to select and configure the frequently used attributes for a profile. The attributes that are included here are those defined by the TACACS+ protocol draft specifications. However, the values can be used in the authorization of requests from other services. In the Task Attribute View, the ISE administrator can set the privileges that will be assigned to the device administrator. The common task types are:
Shell
WLC
Nexus
Generic
The Custom Attributes section allows you to configure additional attributes. It provides a list of attributes that are not recognized by the Common Tasks section. Each definition consists of the attribute name, an indication of whether the attribute is mandatory or optional, and the value for the attribute. In the Raw View, you can enter the mandatory attributes using a equal to (=) sign between the attribute name and its value and optional attributes are entered using an asterisk (*) between the attribute name and its value. The attributes entered in the Raw View are reflected in the Custom Attributes section in the Task Attribute View and vice versa. The Raw View is also used to copy paste the attribute list (for example, another product’s attribute list) from the clipboard onto ISE. Custom attributes can be defined for nonshell services.
New Question
What allows an endpoint to obtain a digital certificate from Cisco ISE during a BYOD flow?
A. Network Access Control
B. My Devices Portal
C. Application Visibility and Control
D. Supplicant Provisioning Wizard
Answer: B
New Question
What occurs when a Cisco ISE distributed deployment has two nodes and the secondary node ,s deregistered?
A. The primary node restarts
B. The secondary node restarts.
C. The primary node becomes standalone
D. Both nodes restart.
Answer: D
Explanation:
https://www.cisco.com/c/en/us/td/docs/security/ise/1-1-1/installation_guide/ise_install_guide/ise_deploy.html
if your deployment has two nodes and you deregister the secondary node, both nodes in this primary- secondary pair are restarted. (The former primary and secondary nodes become standalone.)
New Question
Which port does Cisco ISE use for native supplicant provisioning of a Windows laptop?
A. TCP 8909
B. TCP 8905
C. CUDP 1812
D. TCP 443
Answer: A
New Question
Which of these is not a method to obtain Cisco ISE profiling data?
A. RADIUS
B. HTTP
C. SNMP query
D. active scans
E. Netflow
F. DNS
Answer: D
New Question
Which of the following is not true about profiling in Cisco ISE?
A. Profiling policies are automatically enabled for use.
B. Cisco ISE comes with predefined profiles.
C. The use of Identity Groups is required to leverage the use of profiling in the authorization policy.
D. Cisco ISE does not support hierarchy within the profiling policy.
Answer: D
New Question
Which two default endpoint identity groups does cisco ISE create? (Choose two )
A. Unknown
B. whitelist
C. end point
D. profiled
E. blacklist
Answer: ADE
Explanation:
Default Endpoint Identity Groups Created for Endpoints Cisco ISE creates the following five endpoint identity groups by default: Blacklist, GuestEndpoints, Profiled, RegisteredDevices, and Unknown. In addition, it creates two more identity groups, such as Cisco-IP-Phone and Workstation, which are associated to the Profiled (parent) identity group. A parent group is the default identity group that exists in the system.
https://www.cisco.com/c/en/us/td/docs/security/ise/2-
4/admin_guide/b_ise_admin_guide_24/b_ise_admin_guide_24_new_chapter_010101.html#ID1678
New Question
Which Cisco ISE service allows an engineer to check the compliance of endpoints before connecting to the network?
A. personas
B. qualys
C. nexpose
D. posture
Answer: D
Explanation:
https://www.cisco.com/c/en/us/td/docs/security/ise/2-
1/admin_guide/b_ise_admin_guide_21/b_ise_admin_guide_20_chapter_010110.html
Posture is a service in Cisco Identity Services Engine (Cisco ISE) that allows you to check the state, also known as posture, of all the endpoints that are connecting to a network for compliance with corporate security policies. This allows you to control clients to access protected areas of a network.
New Question
Which default endpoint identity group does an endpoint that does not match any profile in Cisco ISE become a member of?
A. Endpoint
B. unknown
C. blacklist
D. white list
E. profiled
Answer: B
Explanation:
If you do not have a matching profiling policy, you can assign an unknown profiling policy. The endpoint is therefore profiled as Unknown. The endpoint that does not match any profile is grouped within the Unknown identity group. The endpoint profiled to the Unknown profile requires that you create a profile with an attribute or a set of attributes collected for that endpoint. https://www.cisco.com/en/US/docs/security/ise/1.0/user_guide/ise10_man_identities.html
New Question
Refer to the exhibit. Which command is typed within the CU of a switch to view the troubleshooting output?
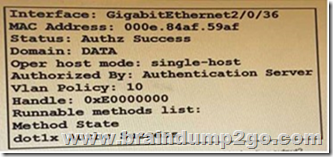
A. show authentication sessions mac 000e.84af.59af details
B. show authentication registrations
C. show authentication interface gigabitethemet2/0/36
D. show authentication sessions method
Answer: A
New Question
What must be configured on the Cisco ISE authentication policy for unknown MAC addresses/identities for successful authentication?
A. pass
B. reject
C. drop
D. continue
Answer: D
Explanation:
https://www.cisco.com/en/US/docs/security/ise/1.0/user_guide/ise10_man_id_stores.html
New Question
Which two probes must be enabled for the ARP cache to function in the Cisco ISE profile service so that a user can reliably bind the IP address and MAC addresses of endpoints? (Choose two.)
A. NetFlow
B. SNMP
C. HTTP
D. DHCP
E. RADIUS
Answer: DE
Explanation:
Cisco ISE implements an ARP cache in the profiling service, so that you can reliably map the IP addresses and the MAC addresses of endpoints. For the ARP cache to function, you must enable either the DHCP probe or the RADIUS probe. The DHCP and RADIUS probes carry the IP addresses and the MAC addresses of endpoints in the payload data. The dhcp-requested address attribute in the DHCP probe and the Framed-IP-address attribute in the RADIUS probe carry the IP addresses of endpoints, along with their MAC addresses, which can be mapped and stored in the ARP cache.
https://www.cisco.com/c/en/us/td/docs/security/ise/2-
1/admin_guide/b_ise_admin_guide_21/b_ise_admin_guide_20_chapter_010100.html
New Question
Which RADIUS attribute is used to dynamically assign the Inactivity active timer for MAB users from the Cisco ISE node?
A. session timeout
B. idle timeout
C. radius-server timeout
D. termination-action
Answer: B
Explanation:
When the inactivity timer is enabled, the switch monitors the activity from authenticated endpoints. When the inactivity timer expires, the switch removes the authenticated session. The inactivity timer for MAB can be statically configured on the switch port, or it can be dynamically assigned using the RADIUS Idle-Timeout attribute
New Question
Which personas can a Cisco ISE node assume?
A. policy service, gatekeeping, and monitonng
B. administration, policy service, and monitoring
C. administration, policy service, gatekeeping
D. administration, monitoring, and gatekeeping
Answer: B
Explanation:
https://www.cisco.com/en/US/docs/security/ise/1.0/user_guide/ise10_dis_deploy.html
The persona or personas of a node determine the services provided by a node. An ISE node can assume any or all of the following personas: Administration, Policy Service, and Monitoring. The menu options that are available through the administrative user interface are dependent on the role and personas that an ISE node assumes. See Cisco ISE Nodes and Available Menu Options for more information.
New Question
What is a characteristic of the UDP protocol?
A. UDP can detect when a server is down.
B. UDP offers best-effort delivery
C. UDP can detect when a server is slow
D. UDP offers information about a non-existent server
Answer: B
Explanation:
https://www.cisco.com/c/en/us/support/docs/security-vpn/remote-authentication-dial-user-service-radius/13838-10.html
Resources from:
1.2020 Latest Braindump2go 300-715 Exam Dumps (PDF & VCE) Free Share:
https://www.braindump2go.com/300-715.html
2.2020 Latest Braindump2go 300-715 PDF and 300-715 VCE Dumps Free Share:
https://drive.google.com/drive/folders/1-jcJT1SxbH3DDB-cgSq_cPEhlxMEfvFK?usp=sharing
3.2020 Latest 300-715 Exam Questions from:
https://od.lk/fl/NDZfMTE4NTEzMl8
Free Resources from Braindump2go,We Devoted to Helping You 100% Pass All Exams!

